Today we are pleased to announce the OnlyKey DUO launch on Kickstarter! With the same features users love about OnlyKey, OnlyKey DUO is one of the most versatile security keys available and in a small form factor that now supports both USB-A and USB-C.

Fast and Easy to Use
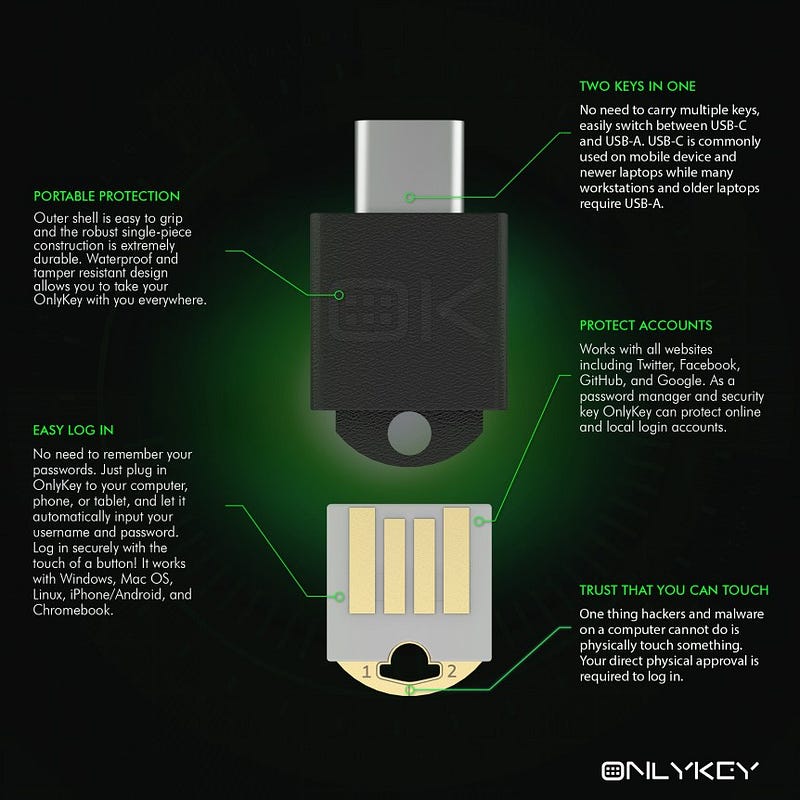
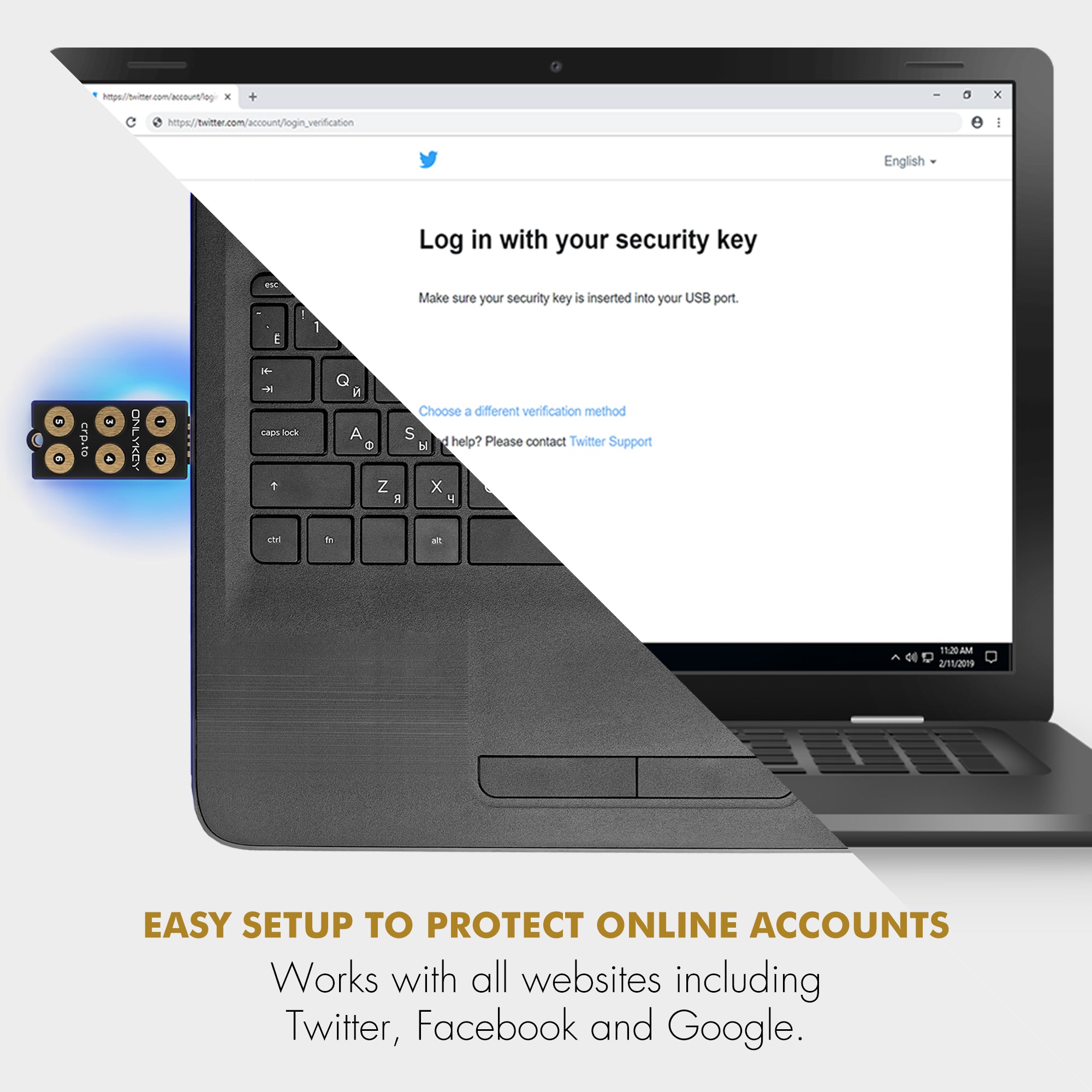
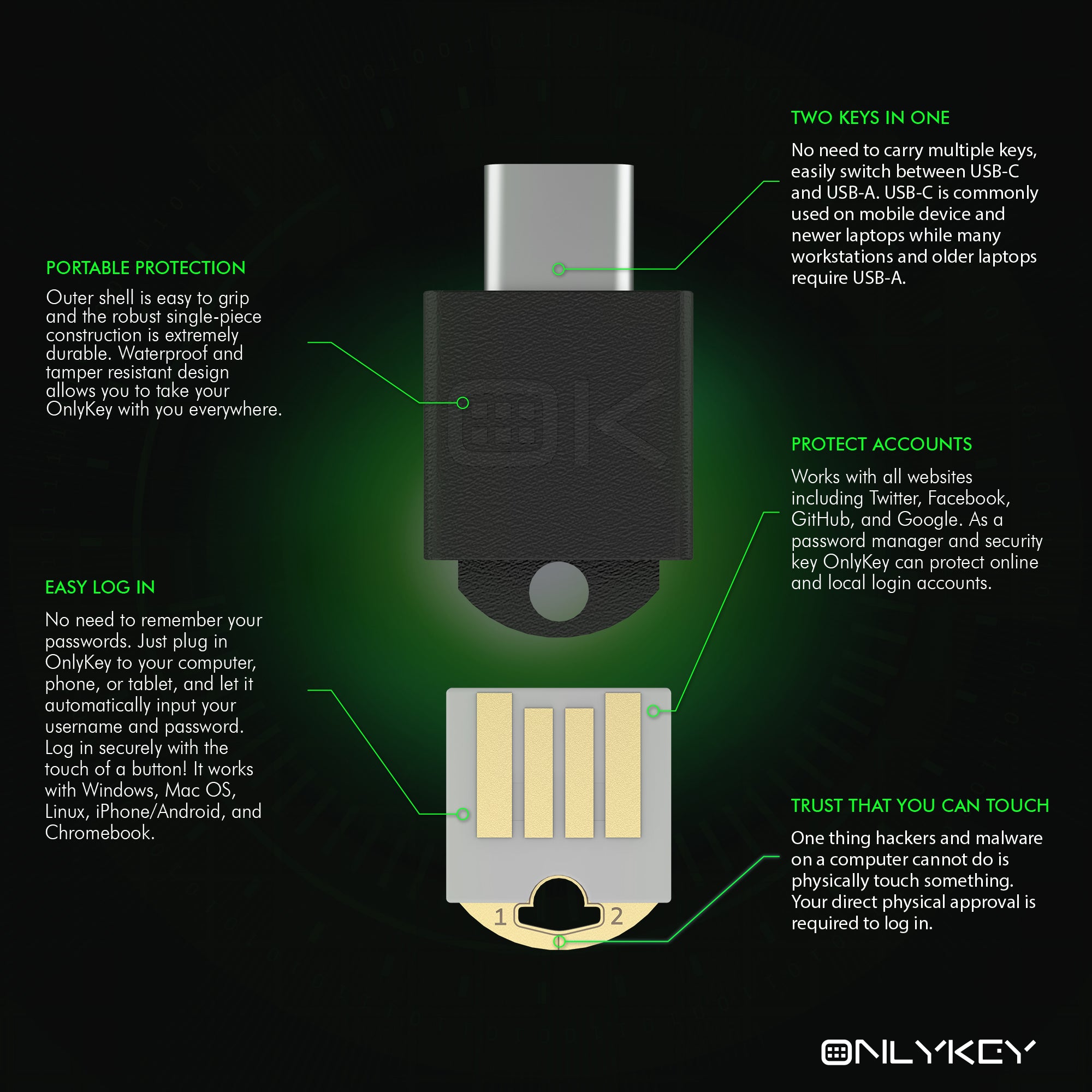
No need to install any software. You can use your OnlyKey DUO immediately for two-factor authentication and passwordless login (FIDO2) supported by major websites such as Microsoft, Google, Facebook, Dropbox, GitHub, Okta, AWS and more. Google and other vendors have recently come out with security keys that support either USB-A or USB-C so users end up buying two security keys or are forced to use an adapter. OnlyKey DUO is like two keys in one. It natively supports both USB types and it is one of the smallest and most portable security keys out there.


Industry-Leading Features
OnlyKey DUO isn’t your run-of-the-mill security key. The proof is in the features. It supports FIDO2 as well as an array of other amazing features such as a hardware password manager, multiple two-factor methods, passwordless SSH login, and OpenPGP. Pre-order OnlyKey DUO from https://www.kickstarter.com/projects/timsteiner/onlykey-duo-portable-protection-for-all-of-your-devices
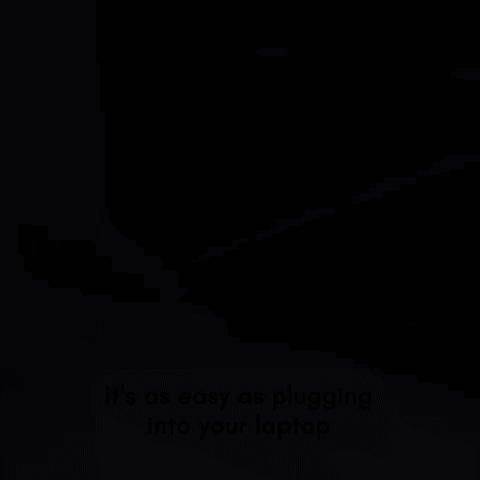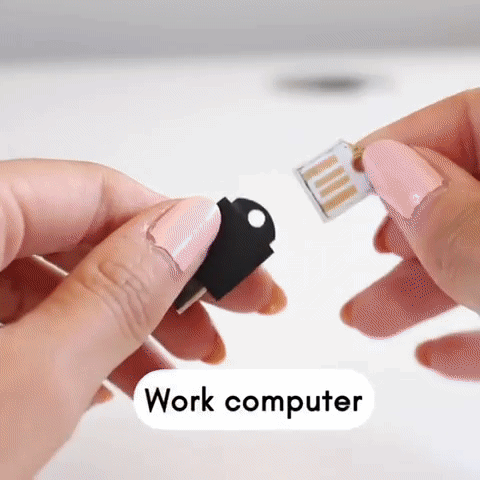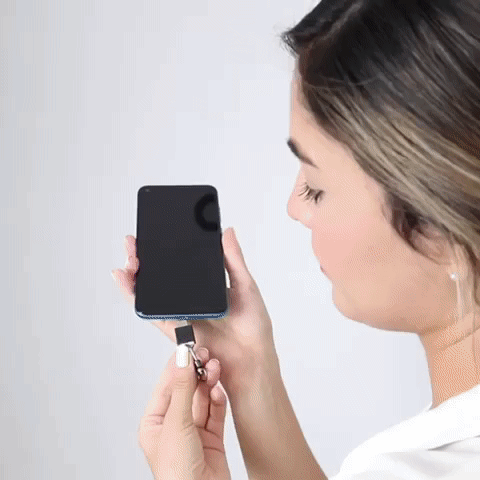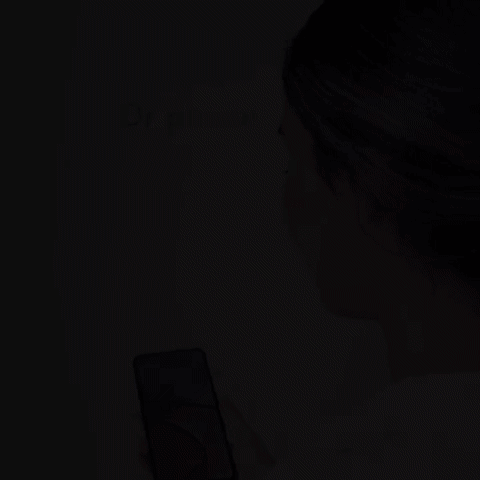














Share:
A More Seamless OpenPGP and SSH Experience with OnlyKey
OnlyKey DUO - The Best Protection For All of Your USB-C and USB-A Devices