Security experts agree that passwords must be long and complex to fend off attackers. But is that enough to protect an organization from hackers and ransomware?
MSPs and small-to-medium-sized businesses are top targets of ransomware attacks. In 2019, at least 13 MSPs were used to push ransomware to clients. Many of these attacks were successful due to password compromise. OnlyKey is a secure hardware password manager and was recently highlighted by ZDNet “Best security key in 2020.”
Long and complex passwords are not enough, to understand why here is how a typical ransomware attack works:
- A user clicks a malicious link in an email which installs malware such as the Emotet trojan.
- The Emotet trojan is used to infect the system with Trickbot or other malware that gathers password hashes from network connected systems and sends them back to the attacker.
- These password hashes are then run through a specialized password cracking device that uses combinations of words, numbers, and special characters to crack passwords. Passwords such as Summer2020!! and CompanyName1234# may be considered long and complex passwords which meet organizational password policies, but they are easily cracked in a matter of minutes or hours.
- Once a workstation or server admin account password is cracked that credential is then used to install ransomware such as Ryuk on all accessible client systems. A ransom that can be up to millions of dollars is demanded to restore client data that is encrypted. Many victims of ransomware may never recover and may even have to close down after an attack.
As you probably guessed, the weak link here is passwords, or more specifically Windows login passwords. Most ransomware is targeted towards Windows systems and the default Windows password policy of uppercase, lowercase, numbers, and special characters results in users selecting weak passwords like Fall2020!. Forcing users to use longer passwords has little effect as February2020! is 13 characters long and is still easily cracked.
How to create passwords that ransomware hackers can’t crack
A good rule of thumb is that if you can remember the password it’s probably not a good password. Software password managers are often used to solve this problem, storing random passwords such as T#%_f6*KAq6A⁷;^ which cannot be reasonably cracked. While software password managers do work well for securing website logins, there are several drawbacks such as you need the software installed on every computer and they don’t work well for Windows/device logins.
Wouldn’t it be great if passwords typed themselves?
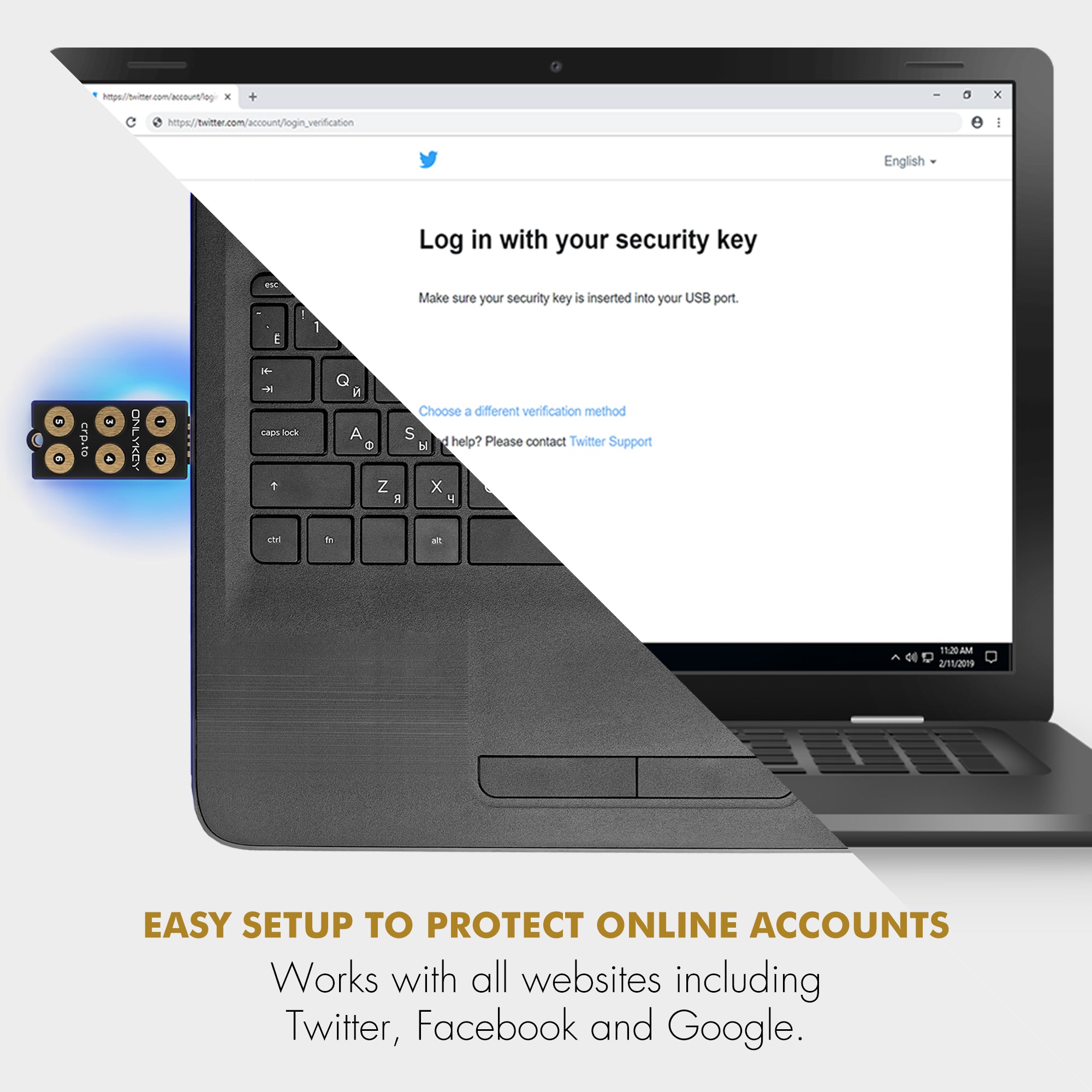
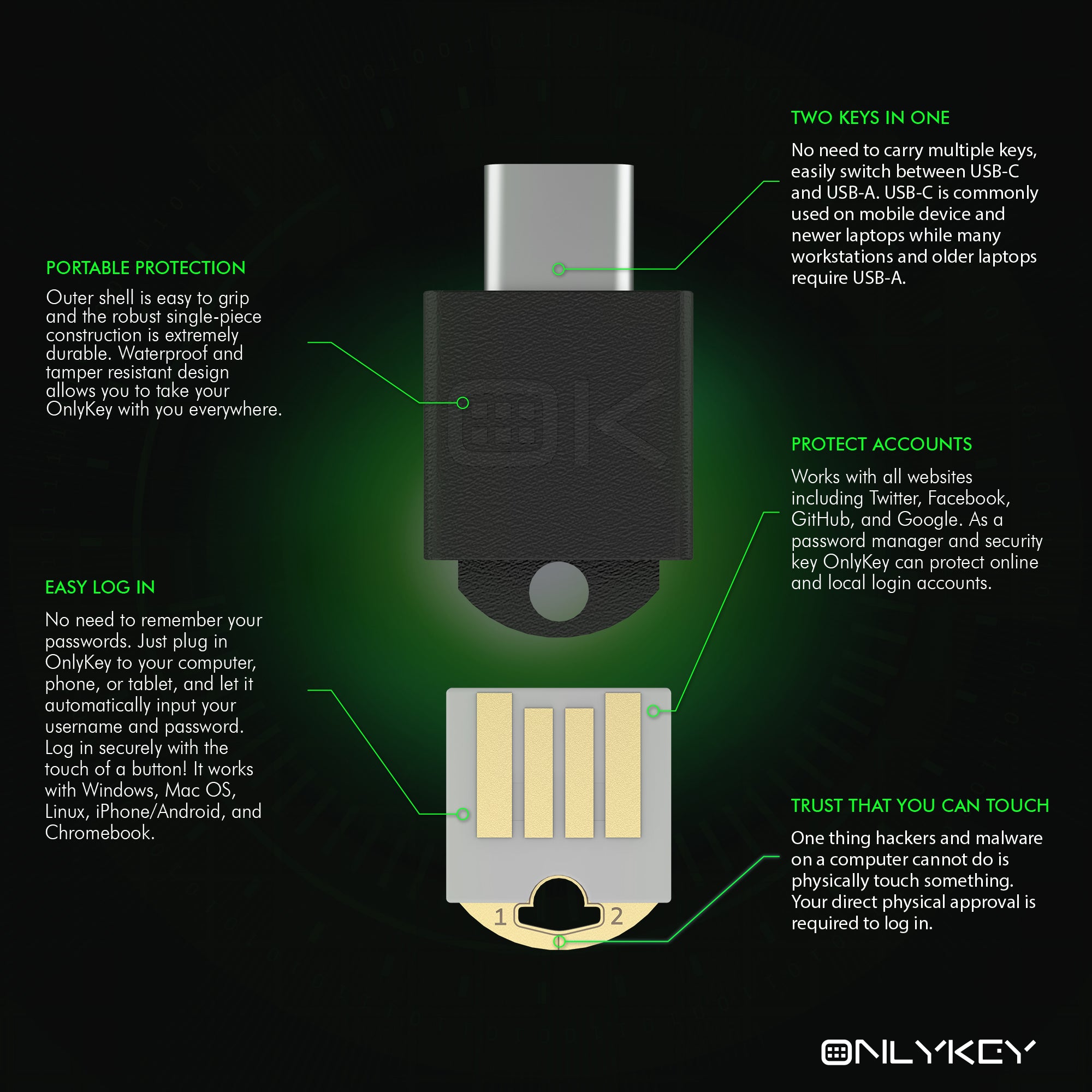
With OnlyKey those strong random passwords can be used for Windows logins or any type of login with no software required. OnlyKey stores up to 56 char long passwords that are stored offline on a physical key fob that is durable, waterproof, and goes everywhere you do.
To protect against ransomware, at a minimum we recommend OnlyKey for:
Power Users — These users may have access to sensitive systems and require strong passwords.
Workstation Administrators — These users have access to workstations and if their password is compromised a ransomware attack would be able to spread to workstations.
Domain Administrators — These users have access to workstations and servers, if their password is compromised a ransomware attack would be able to spread throughout the domain.
OnlyKey not only functions as a hardware password manager but also supports the most common two factor authentication methods such as OATH TOTP, FIDO U2F, and FIDO2. Purchase OnlyKey on Amazon or from our store.
While there is no silver bullet to preventing ransomware, passwords protected by OnlyKey can prevent ransomware from spreading through account compromise.
Originally published at https://crp.to on August 13, 2020.
OnlyKey for MSPs and Ransomware Protection was originally published in onlykey on Medium, where people are continuing the conversation by highlighting and responding to this story.













Share:
OnlyKey Durability Review
OnlyKey Fall 2020 Update