3 in 4 people will have accounts hacked this year due to insecure passwords
OnlyKey isn't your typical 2nd factor security key, its also a hardware password manager.
When it comes to your life, a lot of invaluable data and assets are online and your accounts could be compromised. OnlyKey is the only solution that helps protect all of your accounts with secure hardware.
With OnlyKey, you can do more than just hope your accounts are safe; you can take control of your online security.
PORTABLE PROTECTION
Extremely durable, waterproof, and tamper resistant design allows you to take your OnlyKey with you everywhere (MIL-STD-810 and IP68).
Never worry about losing OnlyKey, it's PIN protected, utilizes professional grade encryption, and supports secure encrypted backup!

AN ALL-IN-ONE SOLUTION
It works with all browsers and is not limited to just browser use. Use it to log into any device, application, or unlock encrypted drives.
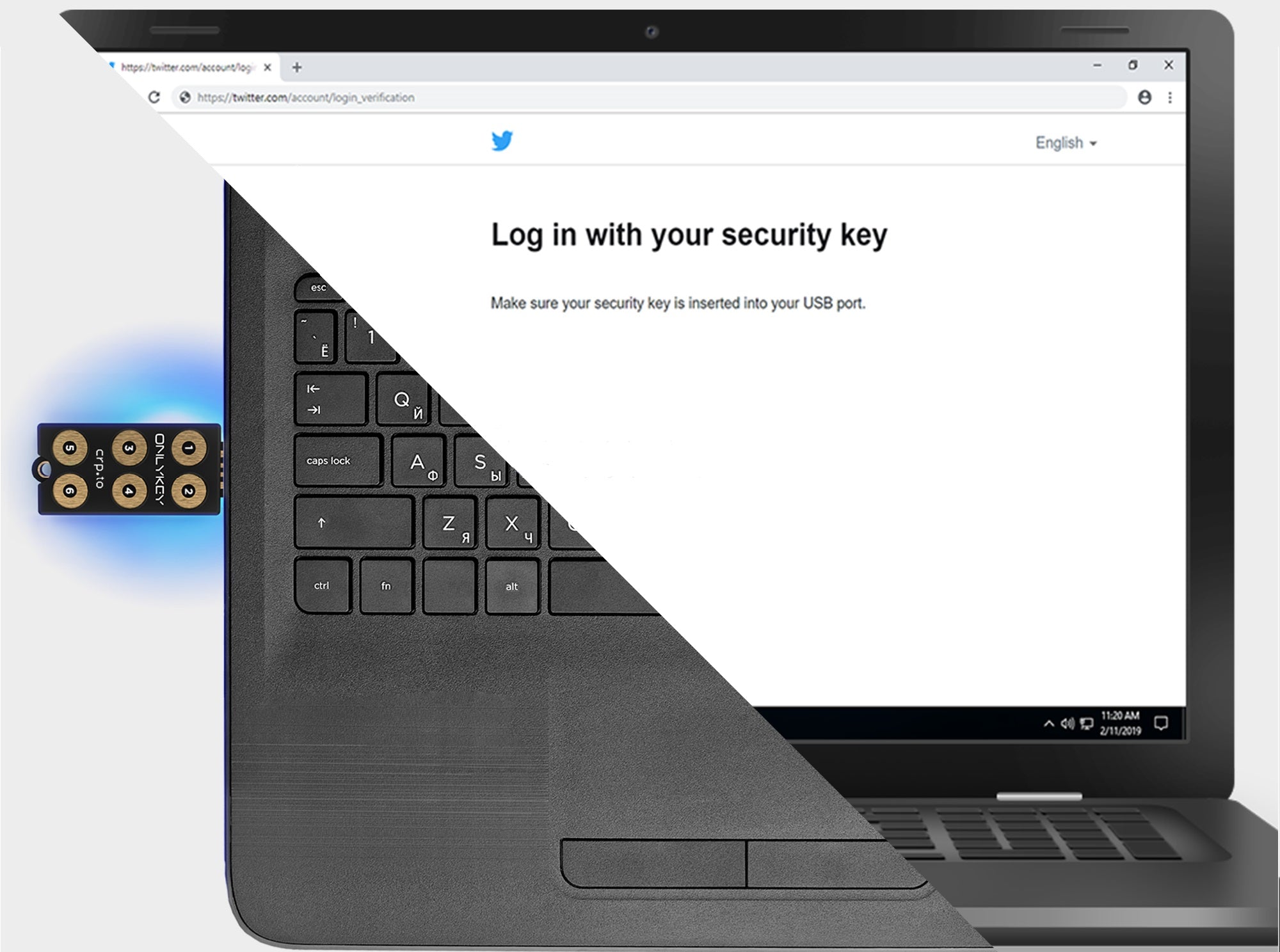
Some sites support OTP codes; others support security keys. OnlyKey does it all and is the most universally supported 2FA key.
You can use your OnlyKey immediately for two-factor authentication and passwordless login (FIDO2) supported by major websites such as Microsoft, Google, Facebook,Dropbox, GitHub,Okta, AWS and more.





OnlyKey
✅ PROTECT ONLINE ACCOUNTS – A hardware password manager, two-factor security key, and file encryption token in one, OnlyKey can keep your accounts safe even if your computer or a website is compromised. OnlyKey is open source, verified, and trustworthy.
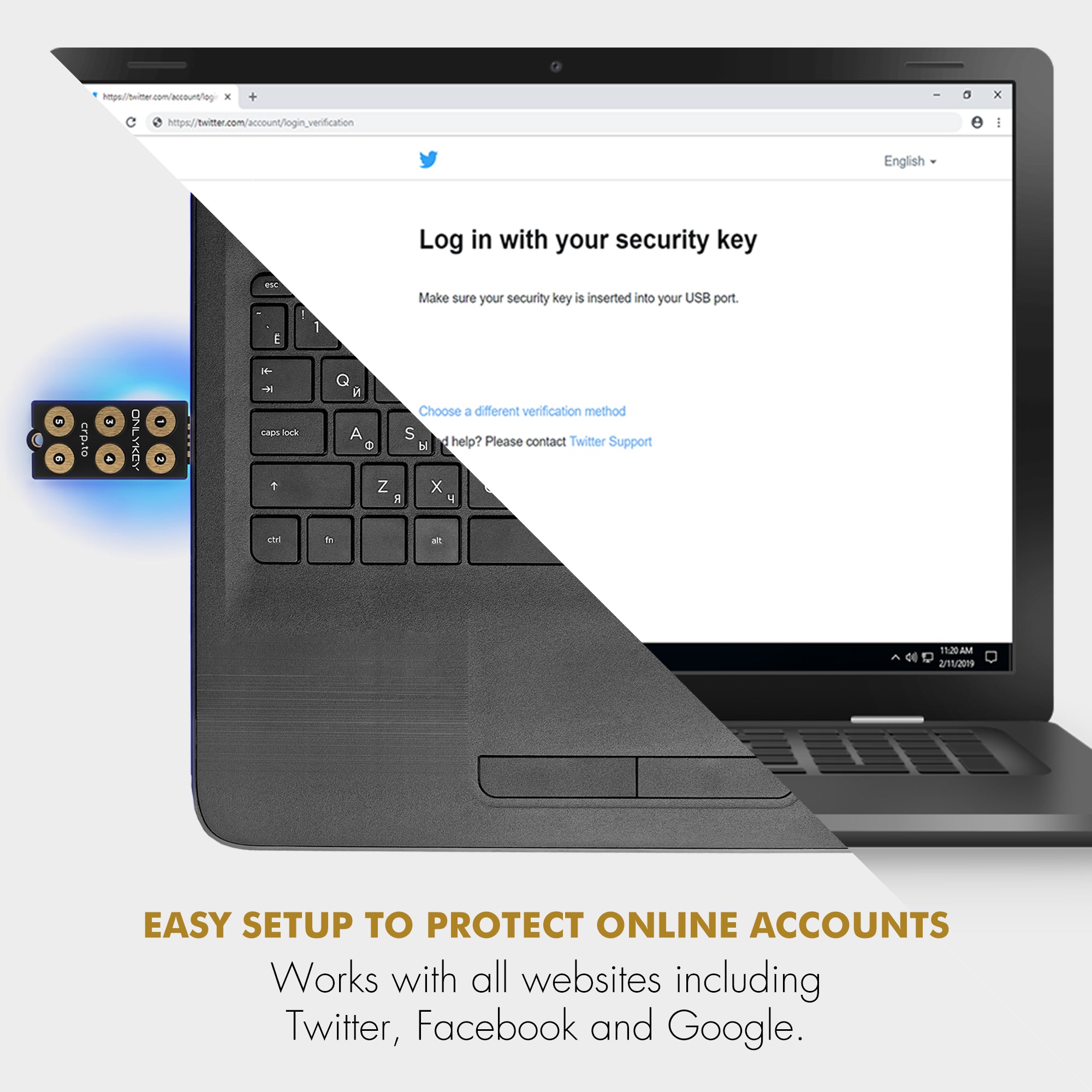
✅ UNIVERSALLY SUPPORTED – Works with all websites including Twitter, Facebook, GitHub, and Google. OnlyKey supports multiple methods of two-factor authentication including FIDO2 / U2F, Yubikey OTP, TOTP, Challenge-response.
✅ PORTABLE PROTECTION – Extremely durable, waterproof, tamper resistant, IP68 and MIL-STD-810G compliant design allows you to take your OnlyKey with you everywhere.
✅ PIN PROTECTED – The PIN used to unlock OnlyKey is entered directly on it. This means that if this device is stolen, data remains secure, after 10 failed attempts to unlock all data is securely erased.
✅ EASY LOG IN – No need to remember multiple passwords because by plugging OnlyKey to your computer, it automatically inputs your username and password. It works with Windows, Mac OS, Linux, or Chromebook, just press a button to login securely!
OnlyKey is made in USA of U.S. and imported parts
Buy on Amazon with free 2-day prime shipping in US

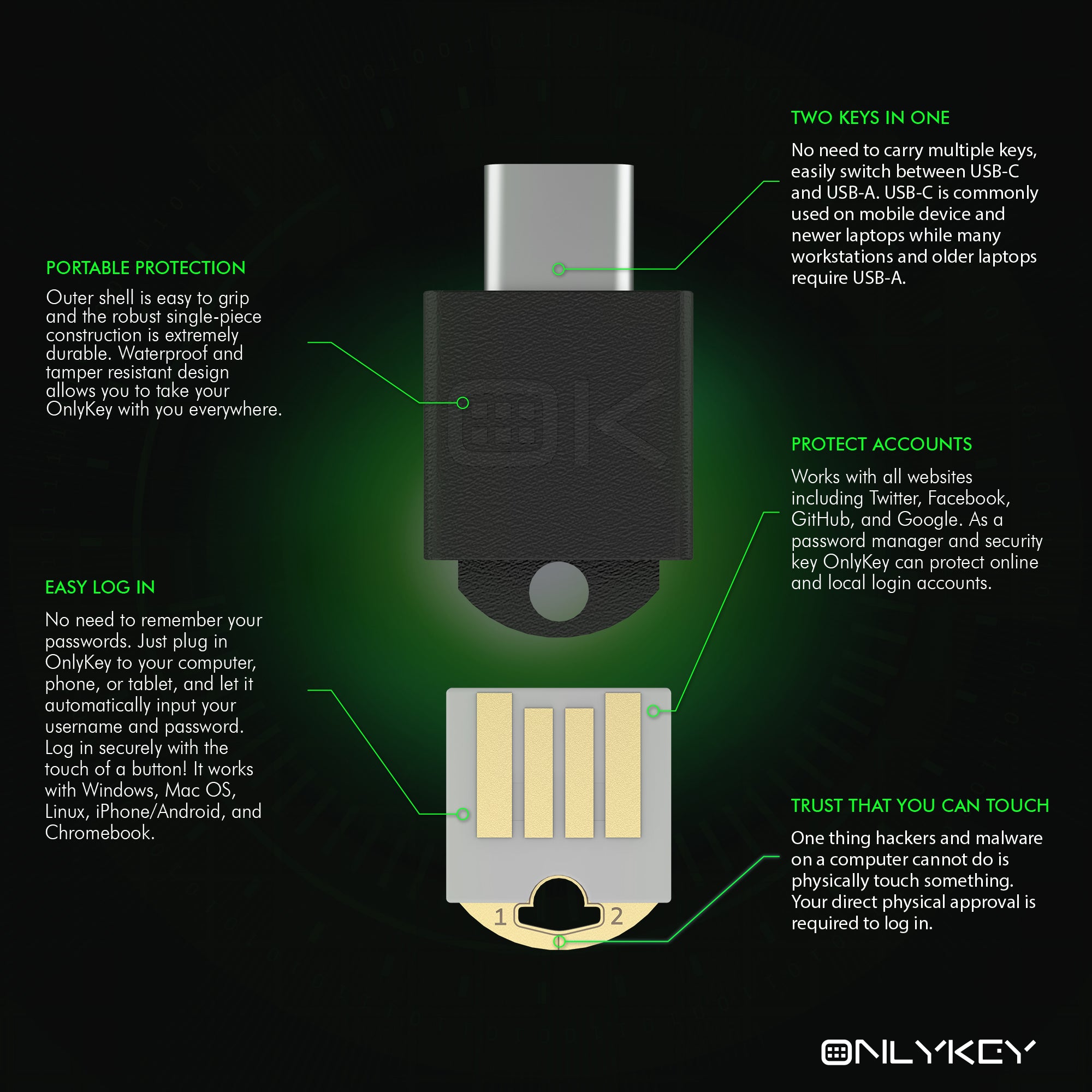




OnlyKey DUO - Dual USB-C and USB-A Security Key
OnlyKey DUO is a USB security key that works virtually everywhere, supporting both USB-A and USB-C. Say goodbye to remembering passwords! Like a security swiss army knife, use as a password manager, MFA (FIDO2, TOTP, and Yubico® OTP), SSH, OpenPGP, and more.
✅ PROTECT ONLINE ACCOUNTS – A hardware password manager, two-factor security key, and file encryption token in one, OnlyKey can keep your accounts safe even if your computer or a website is compromised. OnlyKey is open source, verified, and trustworthy.
✅ UNIVERSALLY SUPPORTED – Works with all websites including Twitter, Facebook, GitHub, and Google. OnlyKey supports multiple methods of two-factor authentication including FIDO2 / U2F, Yubikey OTP, TOTP, Challenge-response.
✅ PORTABLE PROTECTION – Extremely durable, waterproof, tamper resistant, IP68 and MIL-STD-810G compliant design allows you to take your OnlyKey with you everywhere.
✅ EASY LOG IN – No need to remember multiple passwords because by plugging OnlyKey to your computer, it automatically inputs your username and password. It works with Windows, Mac OS, Linux, or Chromebook, just press a button to login securely!
OnlyKey is made in USA of U.S. and imported parts
Buy on Amazon with free 2-day prime shipping in US




Two OnlyKey Starter Pack | ALWAYS HAVE A BACKUP
Make sure to always have a backup of your passwords and accounts with two OnlyKeys. You can easily create a secure backup of your OnlyKey and restore your backup onto your spare device. All starter packs include:
- (2) OnlyKey and/or OnlyKey DUO devices
- (3) Heavy duty keychains
- (1) Portable 2-in-1 USB-A to Lightning and USB-C OTG Adapter
Latest Stories
Interview With Tim Steiner Founder and CEO at OnlyKey
Defragmenting Enterprise Authentication | An Improved Approach to Identity Access Management