“How durable is it?”
This is one of the most common questions I get about OnlyKey. While we have the answer to this question in our FAQ that’s just not quite as gratifying as watching an OnlyKey set on fire and run over by a car. TPIDG recently tested OnlyKey doing just that, check out the review to see how OnlyKey did.
Speaking of questions about OnlyKey durability here are some less frequent ones that I have received and the answers just in case you were wondering.
Q — Will OnlyKey withstand an electromagnetic pulse (EMP) attack?
A — Due to OnlyKey’s simple design and small size it would probably fair better than other electronics like smartphones and computers. In the event of an EMP your OnlyKey may still work but be sure to make a backup if you are expecting an EMP in your area.
Q — Can I wear OnlyKey around my neck for diving and will it withstand salt water?
A — Yes, while we have not tested this specifically there have been reports of OnlyKey being used like this. Rinsing off the salt water with clean water is recommended.
Q — I accidentally ran my OnlyKey through the washing machine will it be OK?
A — OnlyKey is highly water resistant, just make sure to fully dry it off before plugging into a computer.
Originally published at CryptoTrust.
OnlyKey Durability Review was originally published in onlykey on Medium, where people are continuing the conversation by highlighting and responding to this story.



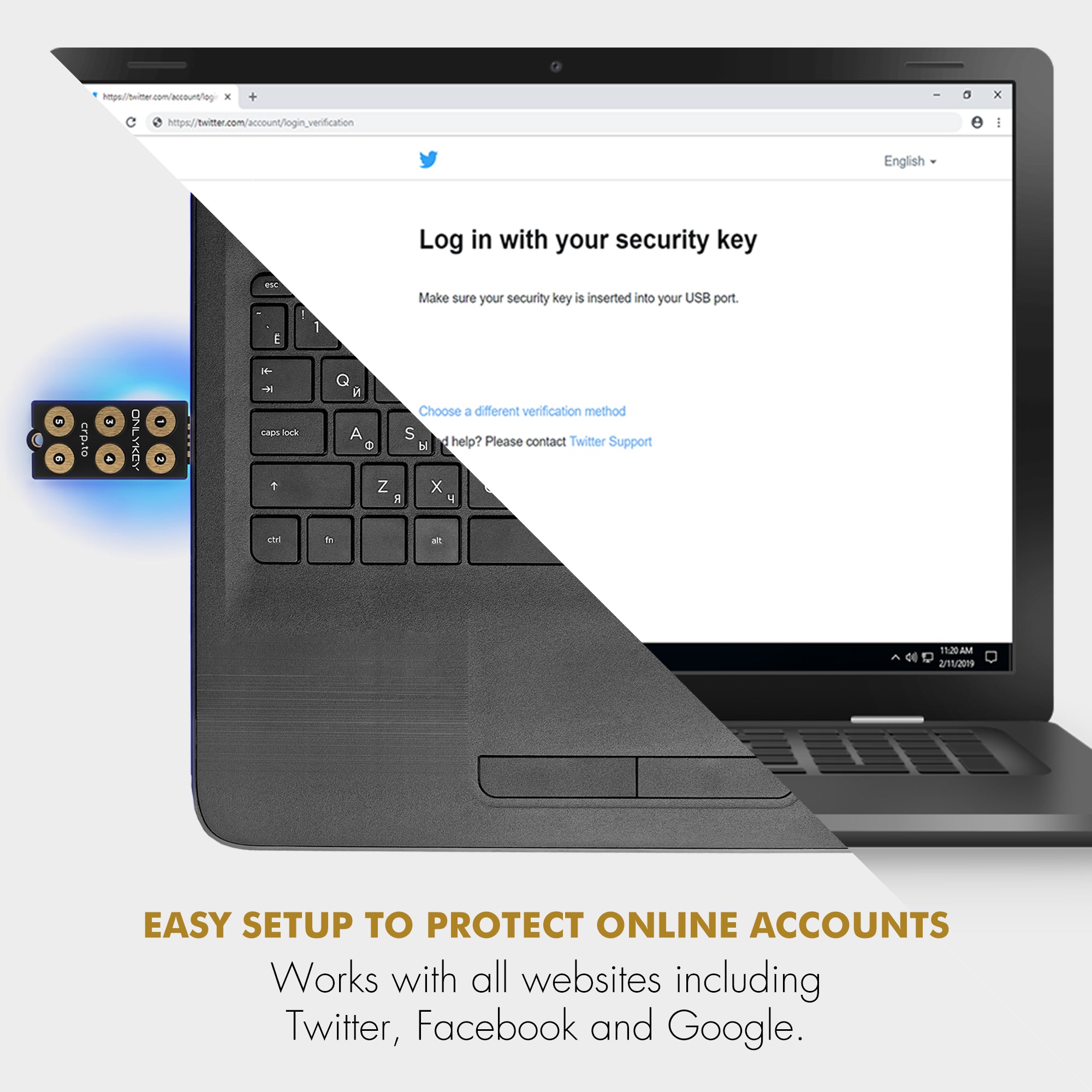


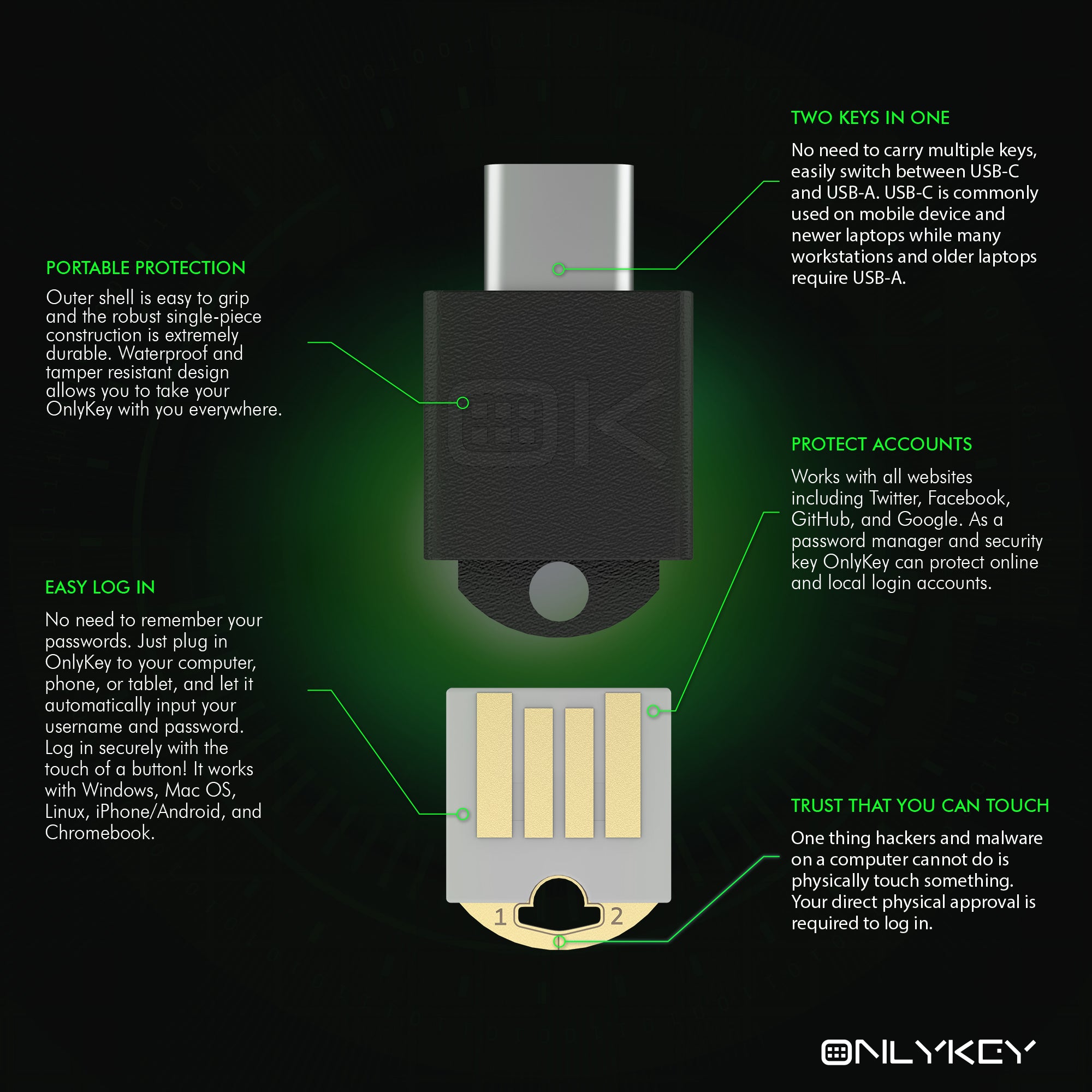








Share:
OnlyKey Beta 7 Release — Blockchains, Bootloaders, and Better OnlyKey Experience
OnlyKey for MSPs and Ransomware Protection