In the ever-evolving landscape of cybersecurity, Chief Information Security Officers (CISOs) face a persistent challenge: securing authentication mechanisms within their organizations. Despite numerous predictions heralding the end of passwords, they remain a cornerstone of digital security. This article delves into the problems of current authentication practices and how a unique piece of hardware may present a viable solution to these critical issues.
The Persistent Problem of User Authentication
The modern enterprise authentication infrastructure is fragmented. Businesses often rely on a patchwork of solutions, from custom-built applications to legacy systems, each requiring its own method of authentication. This fragmentation leads to significant security gaps, particularly in managing multiple complex passwords and ensuring consistent multi-factor authentication (MFA) across all platforms.
A glaring example of this vulnerability is highlighted by the Okta breach in 2023. A single compromised workstation led to unauthorized administrative access, despite Okta's reputation for robust single sign-on (SSO) and passwordless solutions. Improved employee education is a common highlight in post-incident assessments. Here’s the problem: a company’s cybersecurity awareness training can be 99.9% spot-on, but when all it takes is a single mistake from a fatigued employee, even the best employee education will not prevent a breach. This incident underscores the critical need for comprehensive and cohesive identity access management (IAM) solutions that go a step beyond current common practices.
The OnlyKey Solution
As critical systems in every industry become more dependent on information technology, addressing the gaps in IAM becomes increasingly important. OnlyKey emerges as a powerful tool to bridge these gaps. By integrating seamlessly with existing IAM infrastructures, OnlyKey offers a versatile and robust solution for securing enterprise authentication and preventing costly and potentially life-threatening network breaches. Here’s how:
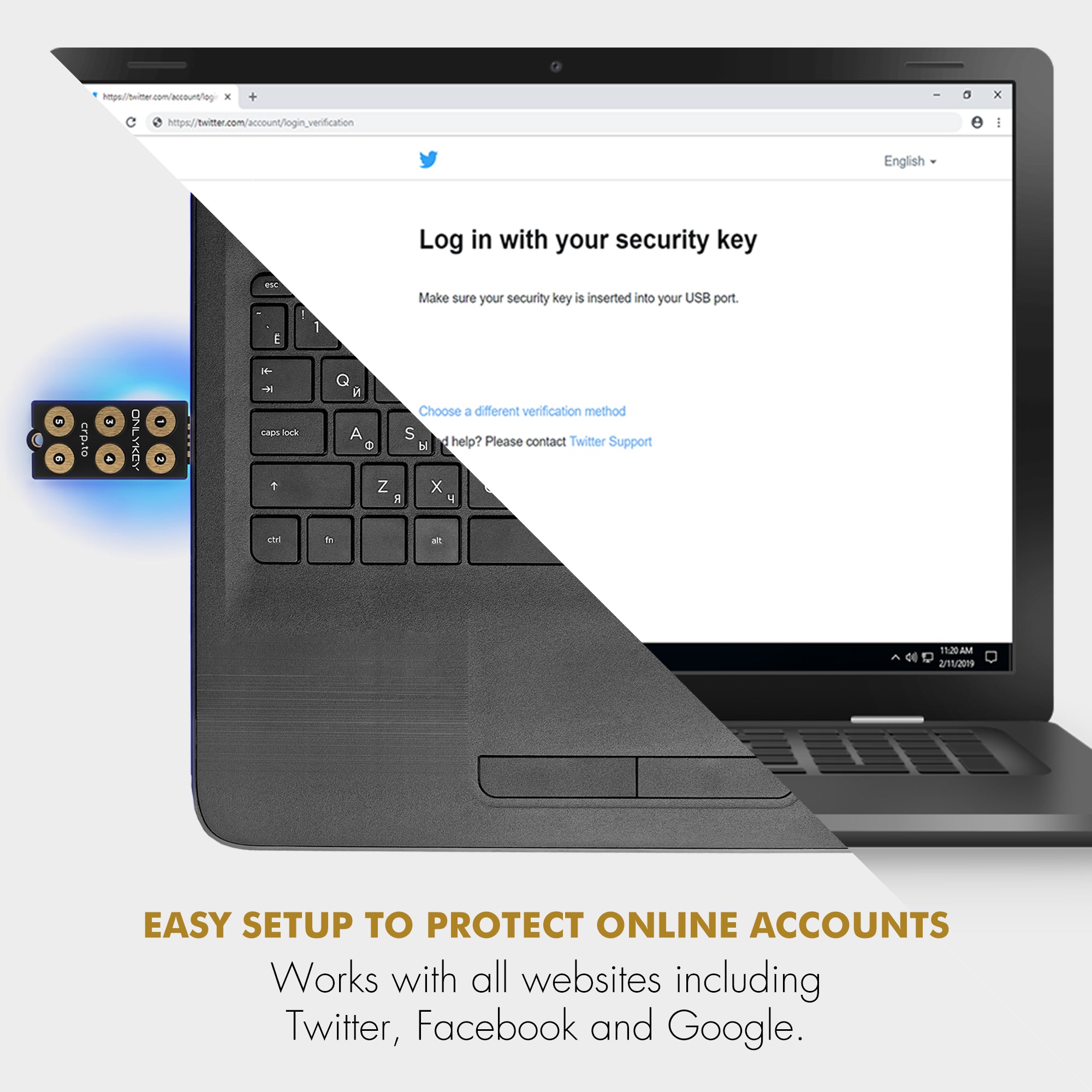
For workstation and server authentication, OnlyKey supports various protocols, such as FIDO2 for Microsoft Entra ID, and works with MFA providers like Authlite for secure offline authentication. This capability ensures that even if a single workstation is compromised, broader system security remains intact.
Local applications often hold critical business data and typically rely on password authentication. OnlyKey not only supports MFA protocols, but also stores and manages complex passwords and facilitates their secure entry into applications. These passwords are stored in secure hardware and are supported by all applications - even legacy applications - to reduce the risk of breaches due to password fatigue and poor password practices.
Utilizing a software password manager is a security best practice per industry standards. This, however, introduces its own set of vulnerabilities as this sensitive repository is often stored online (i.e. LastPass), or on user devices (i.e. KeePass), and is protected by a single master password. In some cases, teams within an organization may share access to a software password manager. While convenient, software password managers may introduce security issues. What happens if the team member’s device that is used to access the software password manager is compromised? This single point of failure reveals that a better solution is needed. Onlykey protects existing software password managers by adding another security layer to their master password.
For managed service providers (MSPs) and system administrators, managing remote systems securely is paramount. OnlyKey’s hardware password manager supports all remote administration tools, ensuring secure and efficient access management even in virtual environments.
Security professionals and developers often handle sensitive keys for encryption and authentication. OnlyKey provides a secure hardware solution for managing these keys, enhancing security without disrupting existing workflows.
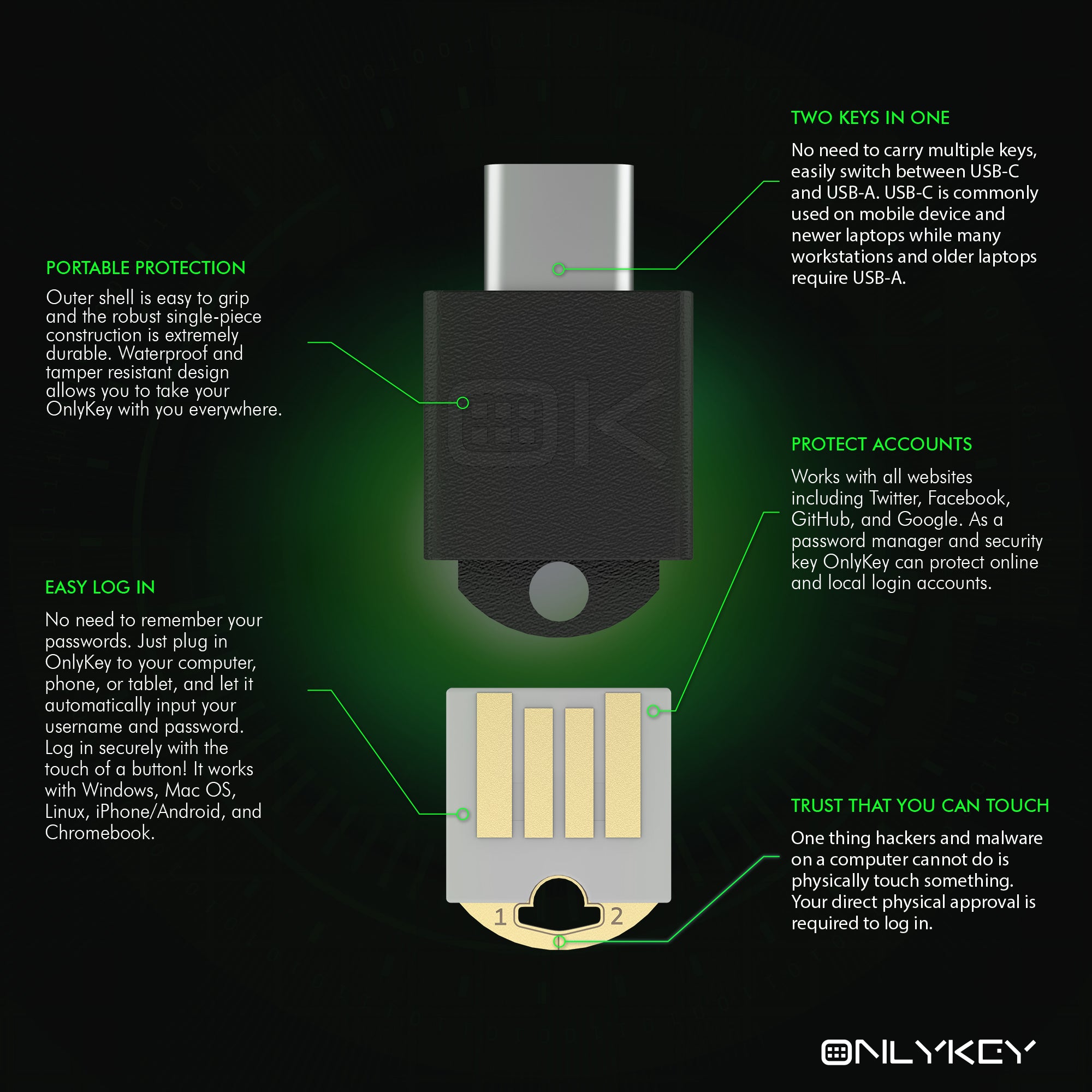
OnlyKey is small, conveniently portable, waterproof, durable, and cannot be used if stolen without knowing its onboard pin. The combination of multiple security layers with user-friendly convenience presents a viable solution for mass distribution within a large network targeted for information theft or ransomware.
Why OnlyKey?
OnlyKey was not the first hardware solution to address access management issues. Yubico’s Yubikey was originally launched in 2008 and quickly rose in the market to become a popular authentication solution. While this and other security keys work well to address access security gaps, they leave much to be desired for large-scale implementation in the long term. This is where OnlyKey innovates with its design, offering robust security features and additional benefits that meet enterprise needs.
OnlyKey can store up to 24 passwords and usernames/URLs, significantly more than Yubikey’s one/two-password limit. Additionally, OnlyKey’s firmware is easily upgradable, ensuring that the device remains up-to-date without the need for replacement, a feature Yubikey lacks. OnlyKey also supports secure backups, allowing users to restore their credentials if the device is lost, a critical capability not available with Yubikey. OnlyKey’s unique hardware pin pad also adds a layer of physical security not available on other security keys.
The Bottom Line
Faster Secure Logins: OnlyKey significantly reduces the time spent on logging into systems where strong passwords are required, with users reporting improved productivity and security.
No Rip and Replace Needed: OnlyKey integrates with existing systems, providing a seamless enhancement to current IAM solutions.
Universal Compatibility: OnlyKey works with a wide range of applications and services, from accounting systems to source code repositories, ensuring comprehensive security coverage.
Proven Track Record: With widespread adoption and positive user feedback, OnlyKey stands out as a trusted solution in the cybersecurity space.
For CISOs, these features translate to enhanced security management, reduced replacement costs, and better resilience against data loss, making OnlyKey a powerful asset for a robust cybersecurity strategy.













Share:
The Fragility of Centralized Services: A Case for Decentralized Solutions
Securing the Future: Comparing YubiKey and OnlyKey in the Evolving Multifactor Authentication Landscape