As cybersecurity threats continue to evolve, multifactor authentication (MFA) has become a critical safeguard for protecting sensitive data. YubiKey security keys are among the most widely adopted tools for MFA, enhancing security by requiring a physical device for user authentication. However, several security vulnerabilities associated with these devices have surfaced over the years, exposing a significant flaw—their inability to receive secure firmware updates.
Vulnerabilities in YubiKey and Google Titan
YubiKeys, particularly the YubiKey 5 series, have become synonymous with secure authentication. Yet, their design lacks a crucial feature: the capacity to update firmware securely. This oversight has led to multiple recalls and security advisories, most notably in 2019 with the YubiKey FIPS series due to a vulnerability that allowed for private key extraction, and more recently with the YubiKey 5 series. The latter incident, disclosed in September 2024 through a detailed report by NinjaLab, highlighted a side-channel vulnerability in the ECDSA implementation, enabling potential key cloning if an attacker had physical access to the device. For further details, refer to the report here. Similarly, in 2021, Google Titan security keys were found susceptible to a side-channel attack that could expose encryption keys to attackers.
The Need for Secure Firmware Updates
The philosophy behind not allowing firmware updates on devices like YubiKeys stems from a security concern: that updating could potentially be compromised. However, this stance inadvertently creates a different security flaw. By not allowing updates, manufacturers are essentially leaving users with devices that, once compromised in design or implementation, can never be fully secured against known vulnerabilities. All security-critical devices require the ability to adapt and address emerging threats.
A Better Alternative: OnlyKey
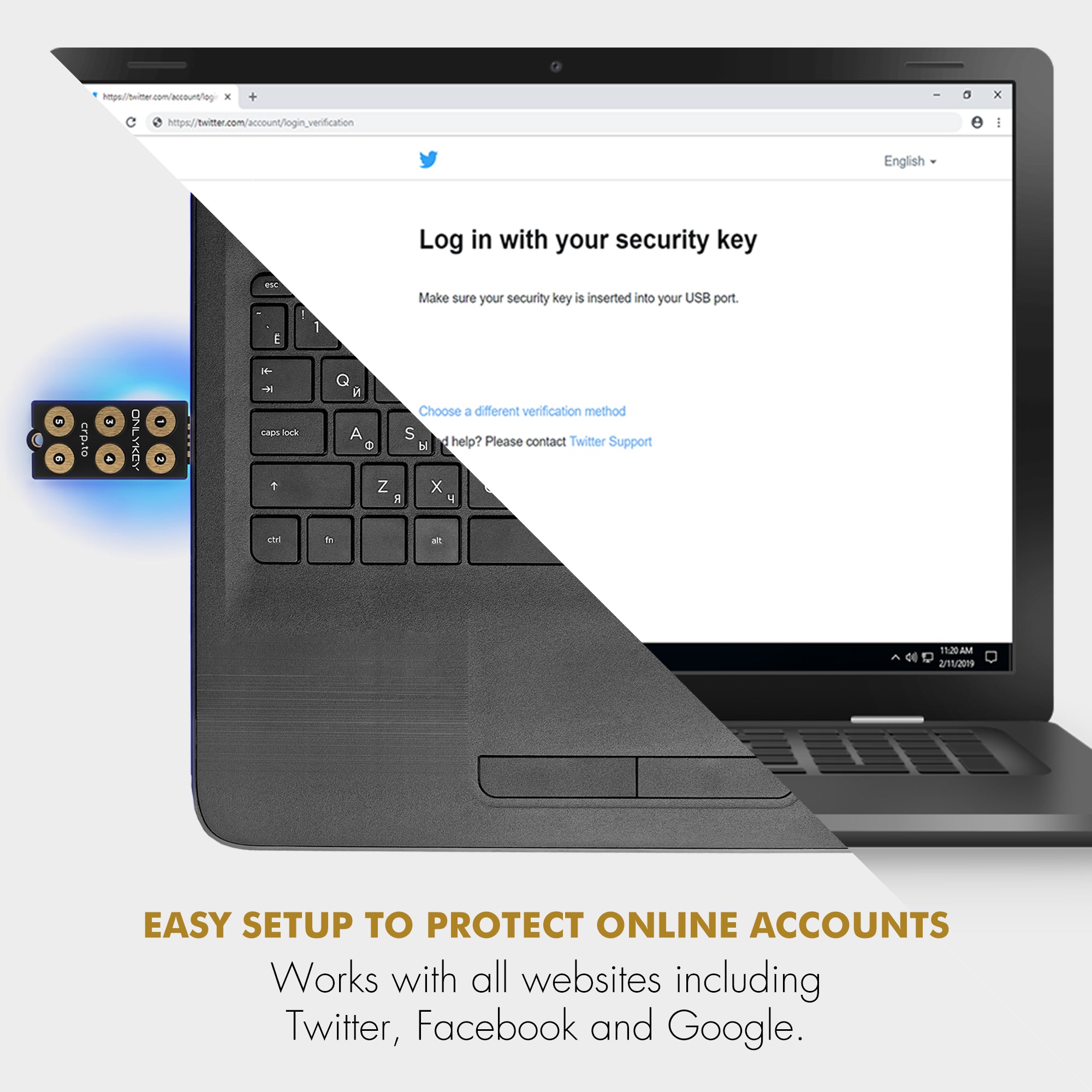
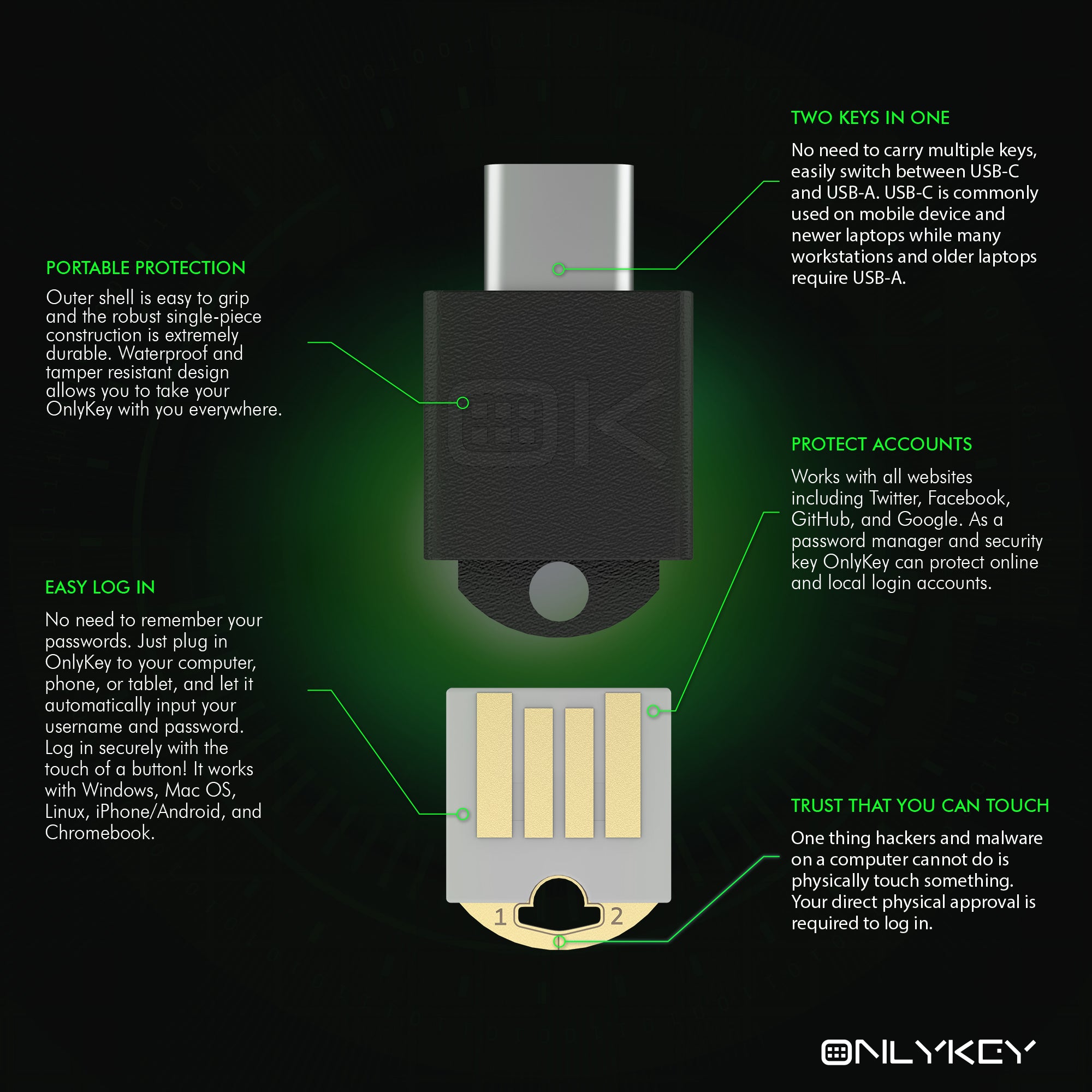
In contrast, OnlyKey, a lesser-known yet highly secure option in the market, has adopted a different strategy. Since its inception in 2016, OnlyKey has supported secure firmware updates. This feature not only allows for patches against newly discovered vulnerabilities but also ensures that users aren't left with out-of-date, potentially insecure devices. Moreover, OnlyKey takes an additional step in user engagement by requiring an email address during setup, enabling direct communication for critical updates or security alerts.
Broader Implications
This scenario raises broader questions about product design in the security sector. Should devices that are pivotal to our digital security be manufactured with the expectation of obsolescence or replaceable parts? Or should they be designed with longevity and adaptability in mind?
The contrast between YubiKey's and OnlyKey's approaches to firmware updates highlights a critical issue in digital security: the necessity for adaptability in security tools. This principle is not just theoretical; it is practically demonstrated in the evolution of another common security tool—our smartphones. Modern cell phones, which increasingly store passkeys and are integral to our security protocols, routinely receive secure firmware updates. These updates ensure that the devices remain protected against new threats, a standard that should be applied to security keys as well.













Share:
Defragmenting Enterprise Authentication | An Improved Approach to Identity Access Management
Interview With Tim Steiner Founder and CEO at OnlyKey