
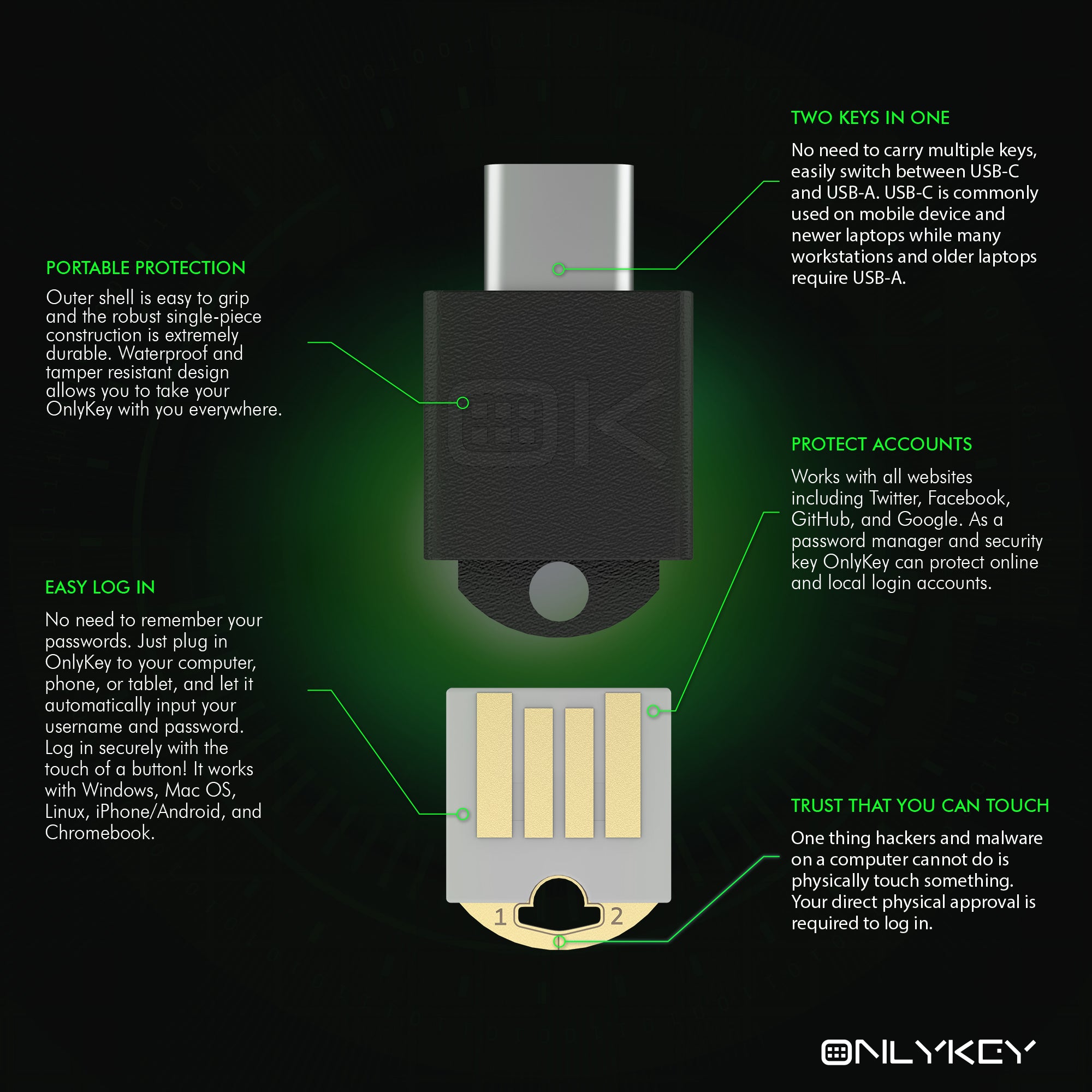
OnlyKey DUO is the newest addition, supporting all of your devices with either USB-A or USB-C, it supports both in one portable key.
OnlyKey supports touch to type passwords or touch to login as a security key (FIDO2):
With industry leading features OnlyKey DUO provides protection from phishing attacks and keeps your digital world safe.
- Hardware-based password manager. It stores and types strong passwords for you. With so many websites and so many log ins, remembering passwords can be impossible. It works with Windows, Mac OS, Linux, Chromebook, iOS, and Android, just press a button to login with secure passwords!
- Hardware-based TOTP. It stores and types OTPs for you. You can use OnlyKey to automatically type your 6-digit TOTP codes instead of an authenticator app.
- Secure firmware upgrades. Receives regular updates and new features.
- OpenPGP and secure encrypted backup. Never worry about losing OnlyKey DUO
- Developer tools. GnuPG support. Sign emails, git commits, software packages, or manage your passwords (gpg-agent with pass and gopass). Protects SSH keys. Authentication, web tunnels, file transfers and more (OpenSSH and SSH-Agent).
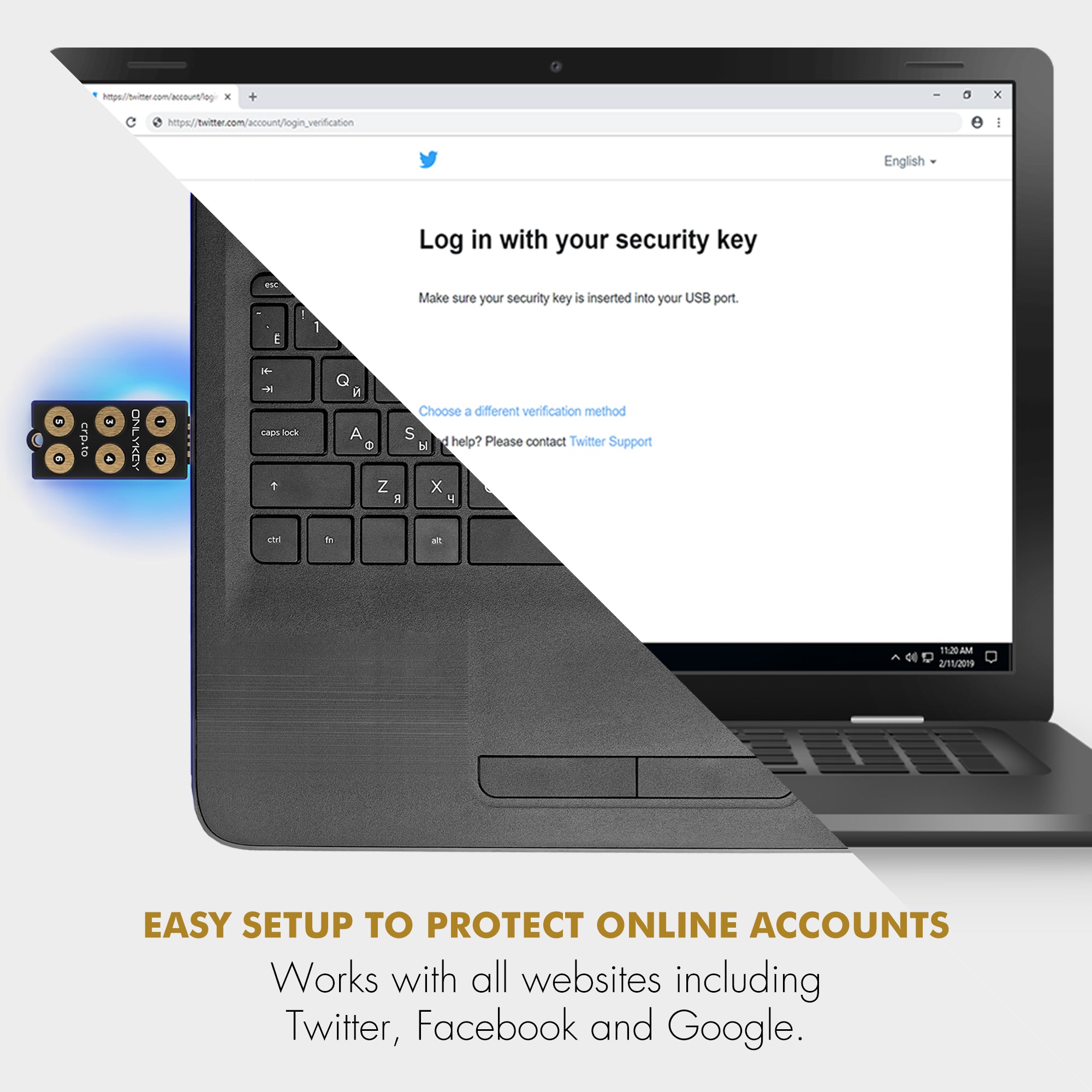
No need to install any software to immediately use as a security key to login to major websites such as Microsoft, Google, Facebook, Dropbox, GitHub, Okta, AWS and more.
Durable, waterproof, and tamper-resistant design allows you to take your OnlyKey DUO with you everywhere.
















Share:
Introducing OnlyKey DUO: The world’s first tiny, portable security key that protects your accounts & works with all your USB-C & USB-A devices right out of the box!
OnlyKey Achieves FIDO2 Certification