Centralized services, while convenient, come with significant vulnerabilities. They require users to trust third parties with their data, creating potential single points of failure. When these systems falter, the repercussions can be widespread and severe. For example, CrowdStrike, a prominent centralized cybersecurity service, crippled computers around the world on Friday, shutting down everything from airlines and television networks to emergency and hospital services.
Risks of Centralized Services
- Single Point of Failure: If the central system fails, the entire service becomes inaccessible.
- Trust Issues: Users must trust the central entity to protect their data, risking data breaches and misuse.
- Regulatory Vulnerabilities: Centralized services are subject to local laws, exposing data to potential government surveillance.
- Scalability Problems: As user bases grow, centralized systems often struggle with performance and reliability.
The Decentralized Alternative: OnlyKey
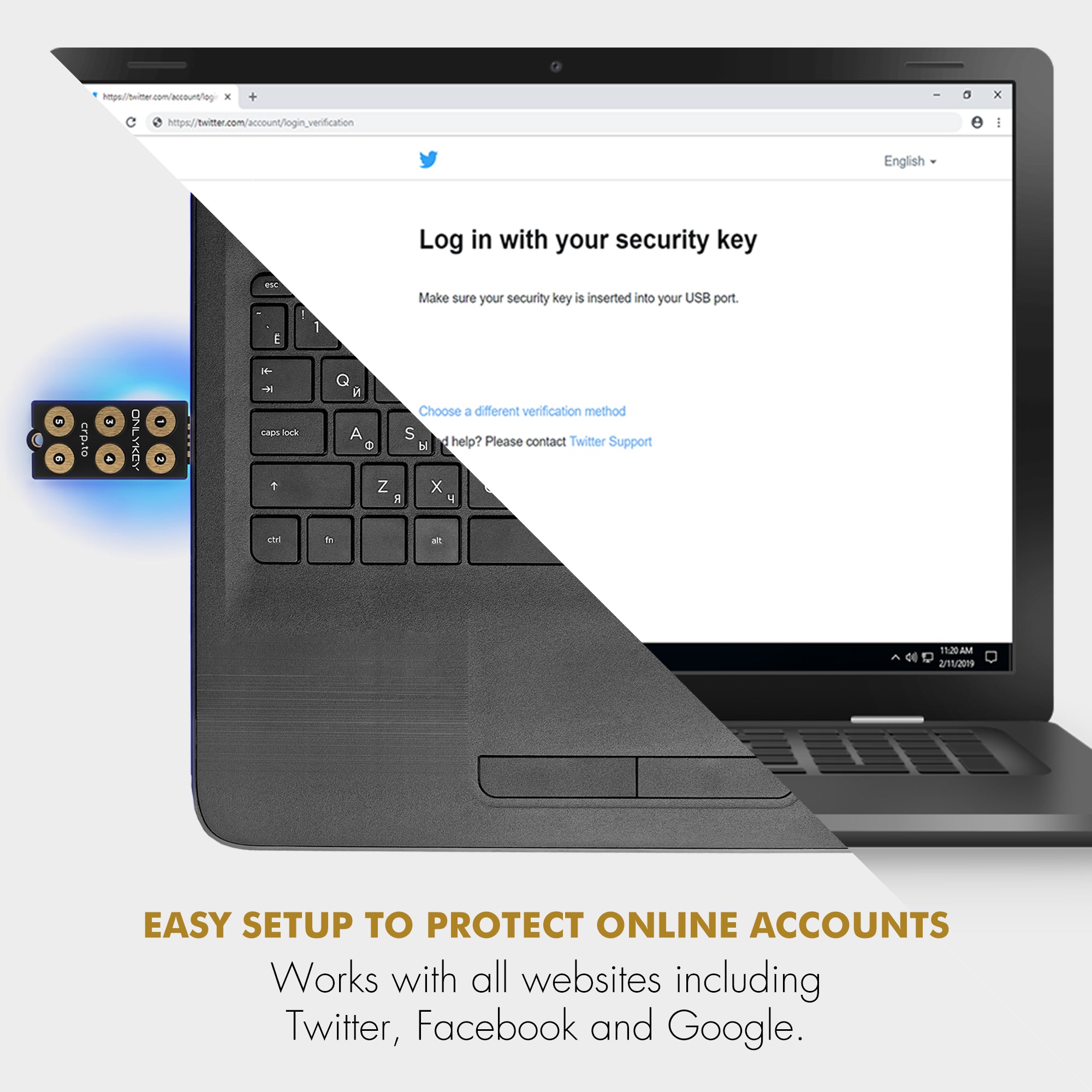
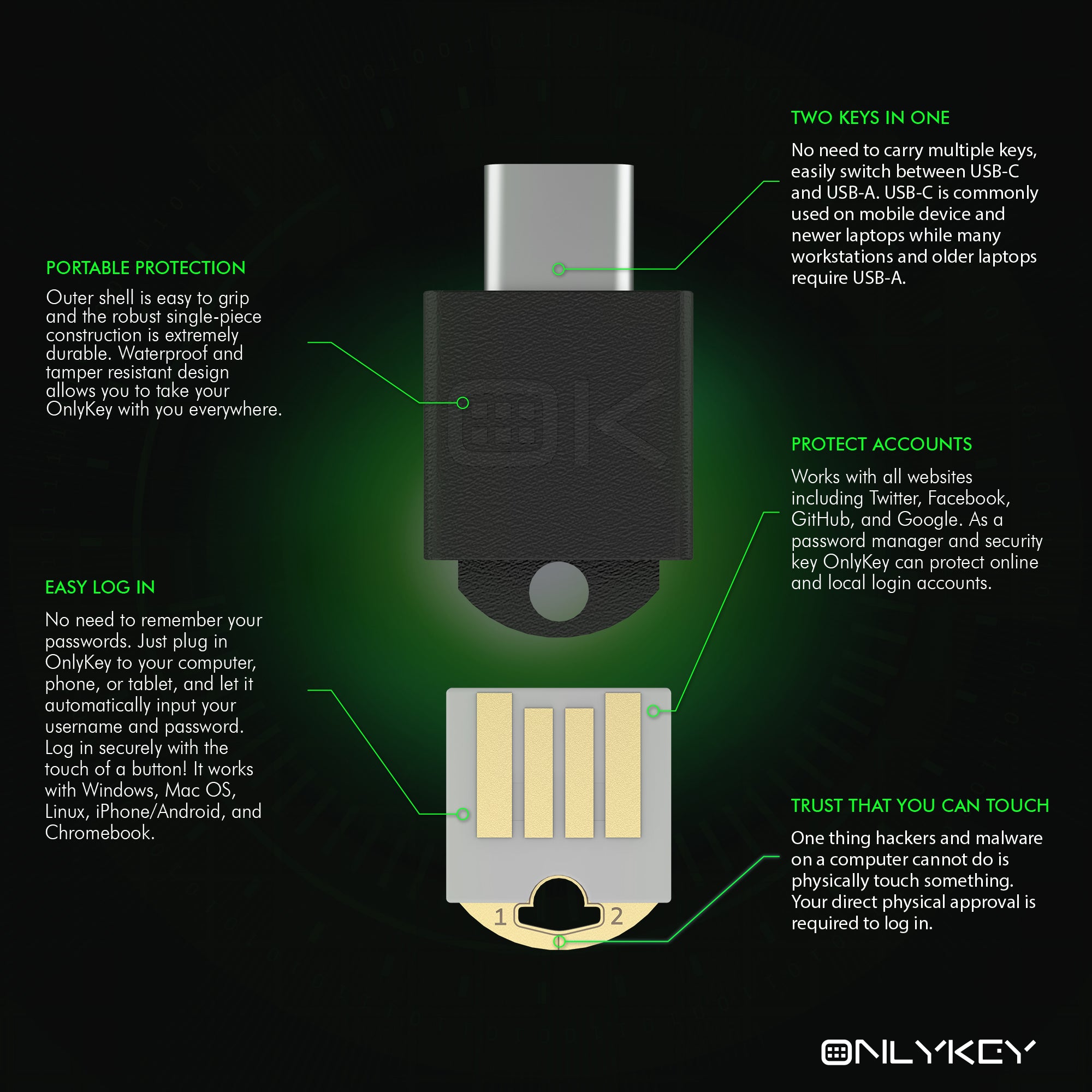
Decentralized solutions like OnlyKey store data locally on secure hardware, not on central servers, ensuring continuous access even when online services fail.
Advantages of OnlyKey:
- No Single Point of Failure: Data is stored on the device, ensuring access regardless of online service disruptions.
- Enhanced Security and Privacy: Users control their data, reducing risks of breaches and misuse.
- Offline Functionality: OnlyKey operates independently, not relying on external services.
- User Control: Complete ownership and control over personal data, free from external interference.
Conclusion
The vulnerabilities of centralized services highlight the need for decentralized solutions. Devices like OnlyKey ensure continuous access to critical account data, mitigating risks associated with central points of failure and third-party trust. Embracing decentralized technologies is crucial for safeguarding data and maintaining digital autonomy in our connected world.














Share:
OnlyKey: The Ultimate Security Tool for Password Managers | Bitwarden, LastPass, 1Password
Defragmenting Enterprise Authentication | An Improved Approach to Identity Access Management