Having hardware protected private keys is the best way and OnlyKey allows easily using these keys with OpenPGP and SSH. To see how this works we will demonstrate creating an OpenPGP key in Protonmail, loading it onto OnlyKey, and then using it with GnuPG. We also have a guide here.
It’s as easy as 1. 2. 3.
1) Create “State of the art X25519 (Modern, fastest, secure)” key in Protonmail
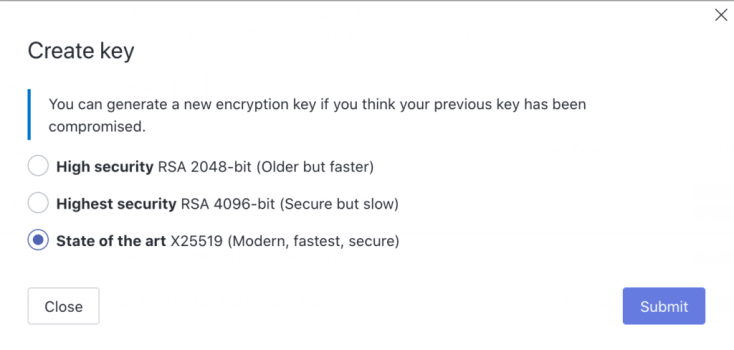
2) Export this key and load key onto OnlyKey using the OnlyKey App
3) Create GnuPG identity with onlykey-gpg, use gpg with your Protonmail, Keybase, or other OpenPGP key securely stored in hardware.
You can do things like sign your emails, git commits, and software packages, manage your passwords (with pass and gopass, among others), authenticate web tunnels and file transfers, and more. Since many 3rd party applications already integrate with SSH-agent and GnuPG you can use those as well.
You can also now use Webcrypt for OpenPGP messages & files on-the-go in the browser
Stored keys on OnlyKey is a great way to securely use OpenPGP and SSH. If you want an even easier option OnlyKey supports derived keys, no OpenPGP key loading necessary. OnlyKey generates the keys for you.
For SSH there is an additional option, OpenSSH as of version 8.2 supports FIDO2 resident keys. Use OnlyKey to store SSH keys that can be used directly in in OpenSSH by following our guide here.





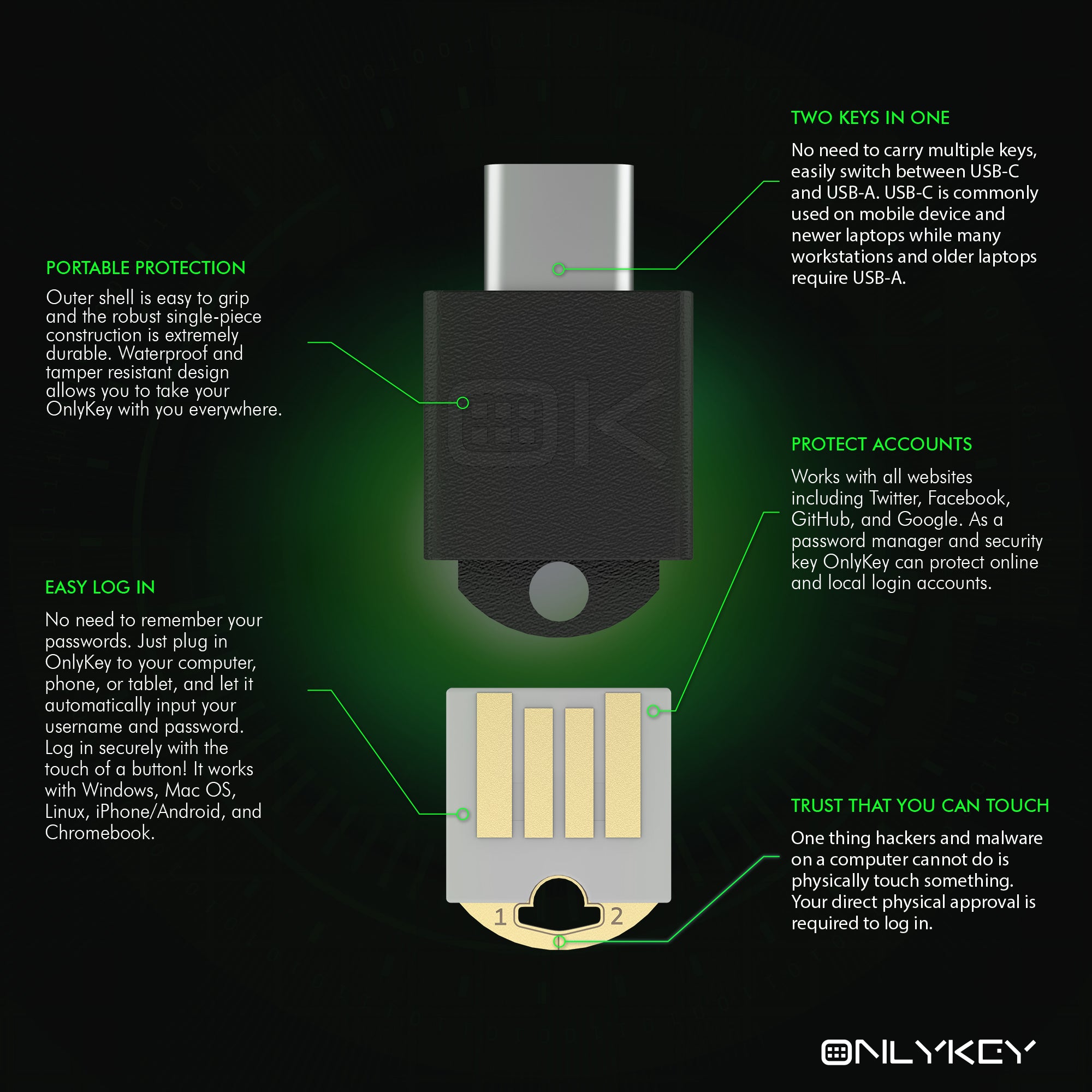








Share:
New OnlyKey Features – Enterprise Windows Active Directory 2FA with Authlite & OpenSSH 2FA Support (ed25519-sk)
Introducing OnlyKey DUO: The world’s first tiny, portable security key that protects your accounts & works with all your USB-C & USB-A devices right out of the box!